 Many thanks to SWLing Post contributor, Franco (K4VZ) , who writes:
Many thanks to SWLing Post contributor, Franco (K4VZ) , who writes:
Just a quick note to let you and the SWLing post readers know about the news of a backdoor in the KiwiSDR software that for years “gave root to project developer”.
For years, a backdoor in popular KiwiSDR product gave root to project developer
Users are rattled after learning their devices and networks were exposed.
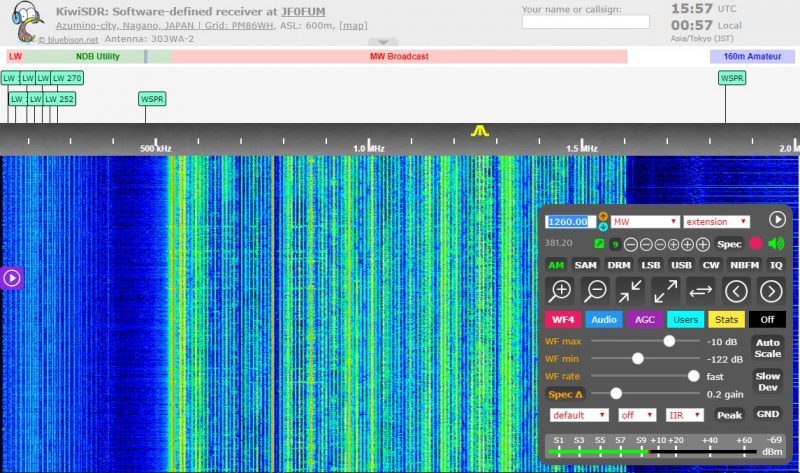
KiwiSDR is hardware that uses a software-defined radio to monitor transmissions in a local area and stream them over the Internet. A largely hobbyist base of users does all kinds of cool things with the playing-card-sized devices. For instance, a user in Manhattan could connect one to the Internet so that people in Madrid, Spain, or Sydney, Australia, could listen to AM radio broadcasts, CB radio conversations, or even watch lightning storms in Manhattan.
On Wednesday, users learned that for years, their devices had been equipped with a backdoor that allowed the KiwiSDR creator—and possibly others—to log in to the devices with administrative system rights. The remote admin could then make configuration changes and access data not just for the KiwiSDR but in many cases to the Raspberry Pi, BeagleBone Black, or other computing devices the SDR hardware is connected to.
A big trust problem
Signs of the backdoor in the KiwiSDR date back to at least 2017. The backdoor was recently removed with no mention of the removal under unclear circumstances. But despite the removal, users remain rattled since the devices run as root on whatever computing device they’re connected to and can often access other devices on the same network.
“It’s a big trust problem,” a user with the handle xssfox told me. “I was completely unaware that there was a backdoor, and it’s hugely disappointing to see the developer adding backdoors in and actively using them without consent.” [Click here to continue reading the full article…]
Thank you for sharing this, Franco (and many other readers who’ve recently shared this article.
I’ve always been a big fan of the KiwiSDR network and the receiver so, of course, this is disappointing news. It sounds as if there’s no evidence the developer did anything nefarious through this root access backdoor, but they were also well aware it existed. That is, without question, a huge security issue.
The KiwiSDR developer comments here on the SWLing Post so my hope is that, perhaps, they can shed some light on this story in our comments section.
Not cool what he did.
If he was a big corporation, he’d be hunted by an army of lawyers.
I don’t believe John, the developer of the KiwiSDR, had any malicious intent in building this feature. But that said, it’s absolutely, 100% unacceptable. I can’t even get my head around how anyone with any knowledge of IT (which every developer has!) would ever think this was OK.
I have a Kiwi that I’ve been planning to open to the public and once I started hearing rumors that there might be a developer’s back door, I decided to wait until I knew more. Even when I do eventually open my Kiwi to the world I’m now going to put it in its own isolated VLAN with no access to my internal network and minimal access to the rest of the internet. I love the KiwiSDR – it’s rekindled my love for shortwave radio – but I no longer trust it to be a “good citizen” on my network.
> “I can’t even get my head around how anyone with any knowledge of IT (which every developer has!)”
In my experience in general, and with the world of ham & radio software in particular, that’s a pretty big assumption! A lot of it – even from supposedly ‘experienced’ developers – is pretty dire in respect of basic security.
(At the risk of upsetting the developer, it’s also pretty obvious that KiwiSDR hasn’t historically had the best relationship with some of the Open Source & software developers it has relied on / benefitted from…)
You’re not wrong about ham devs – a lot of them seem to just have no idea when it comes to security, or they just don’t care. I get that it’s not the “fun” part of writing ham software, but it’s not optional in today’s environment.
Yeah, I’ve read about some of the drama between developers a few years back. It sounds like that was resolved to the satisfaction of both parties eventually, but it’s still indicative of a certain degree of tone-deafness.
I’m really bothered by the fact that the Kiwi dev is planning on releasing closed-source updates in the future. He’s bothered by the existence of cheap Chinese “rip-offs,” but that’s going to happen with any successful product, open-source or not. Part of what I liked about KiwiSDR was its open-source nature, so this movement toward a closed-source approach really irks me. Also, it’d make it a lot harder to confirm the existence of any back doors that might appear in the future.
I was aware of the potential issue of security with the kiwi from the start so I put them on a separate 4G modem to the house so if someone did get in there’s not a lot they can do. One reason my NAS does not have internet access is due to the potential issue with security.
windows has 1000s more security holes along with the software we install + mobile phone and apps.
There’s no way I’m not going to use my Kiwis or block them from the internet, the developers have done a fantastic job with it through the years.
The top companies in the world worth billions or a trillion like microsoft, Facebook, apple and they’ve had far more serious issues, anything connected to the internet can be hacked, in this case it was a deliberate back door but even so people have got to be much more vigilant with their data and not click accept to the terms and conditions of each and every mobile phone app which are notorious at collecting data.
Now I see the kiwi site is down 🙁
Some time ago John (the developer) helped me with an issue, he accessed the KIWI and gave me valuable insight into how to fix the issue. Via a back door? – I don’t know. What developer takes the time to come in and help like that – virtually no one. I do know that if the guy that found the so called back door password vulnerability would have advised John on how to to make it more secure instead of telling the world, we’d all be better off (and still have support!) Then brag about what you found… Sheeeshhh.
The backdoor has been been known for a few years and people have made him aware of it, which means the developer had plenty of time to fix it. The fact that he didn’t means he either doesn’t understand enough about software, or doesn’t care enough about the end users to do the work to make it secure. Either way that is incredibly discouraging to hear about the project, and no way in heck would put one of these on my network.
This wasn’t even an accidental back door – it was 100% intentional.