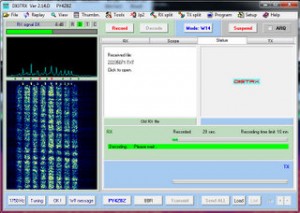
 A few weeks ago, I published a post with a recording of the Cuban numbers station HM01, a “Hybrid Mode” numbers station which interchangeably broadcasts both voice and a digital mode called RDFT with each transmission. I had suggested using an application called “DIGTRX” to decode the data bursts.
A few weeks ago, I published a post with a recording of the Cuban numbers station HM01, a “Hybrid Mode” numbers station which interchangeably broadcasts both voice and a digital mode called RDFT with each transmission. I had suggested using an application called “DIGTRX” to decode the data bursts.
I then received a comment on that post from the author of the DIGTRX program himself, Roland. He has actually created a page in English which describes in detail how to decode the RDFT in HM01. Note that this page was originally in Roland’s native Portugese, and he kindly translates it into English for us: http://www.qsl.net/py4zbz/eni.htm
[While this means that we can decode the transmissions, it doesn’t mean we can necessarily decipher them, however. At least, not yet.]
Imagine that a spy numbers station is using an application you, yourself, authored to send coded messages. What are the odds? This apparently happened to Roland, when he discovered that HM01 was, in fact, using his application DIGTRX. What?!?
Actually, it makes sense to me that numbers stations would use DIGTRX. After all, it’s open source. Operatives in the field can download the application without raising awareness. If it were a proprietary application, either commercially or of their own design, it would add to the complication of downloading and using it (on both ends). As you’ll read in Roland’s tutorial, HM01 has built in robust redundancies by using RDFT and DIGTRX. Very interesting.
Thanks, Roland, for sharing!